Securing Modern E-Commerce Applications in 2021

In 2013, Target’s retail and e-commerce servers were breached. The attackers stole 40 million customer credit card numbers and damages totaled more than $162 million. The root cause ended up being poor security practices within Target’s IT and software development teams.
According to a report by Krebs on Security, “Once inside Target’s network, there was nothing to stop attackers from gaining direct and complete access to every single cash register in every Target store.” While Target’s challenges were compounded because they had in-store and cloud assets to protect, the lesson is clear for all of us working in e-commerce: security must be a top priority.
In this article, I’ll share some of the major security concerns e-commerce developers should be aware of. Whether you’re using a modern third-party platform or implementing your own microservices, many e-commerce security concerns are universal. By the end of this article, you’ll have a starting point for building a scalable, secure e-commerce application.
[toc-embed headline=”Understanding E-Commerce Security Threats”]
Understanding E-Commerce Security Threats
In order to protect your e-commerce application, you need to be aware of the likely attack vectors. Some of the most common security threats in e-commerce software include:
- Cross-site scripting (XSS) – Cross-site scripting is a vulnerability in which the hackers insert malicious scripts into trusted websites. These attacks can spoof cookies and sessions or steal inputs like usernames and passwords. In e-commerce, these attacks are most dangerous when applied to checkout or login flows.
- Distributed Denial of Service (DDoS) – DDoS attacks can take your website down by overwhelming it with more traffic than the server or network can handle. In doing so, a DDoS attack will bring sales to a halt for hours or days until you can get the malicious traffic under control. While less likely to directly steal data from users, it’s hard to build trust with customers if your website is down.
- Man in the Middle – MitM attacks allow hackers to listen in on calls between two computers. If you’re using a typical front and back end architecture, that might mean attackers can monitor API calls between your frontend and APIs. If you’re using microservices, attackers could infiltrate your network and read calls between your internal services.
- Malware Injection – Malware is installed on your server that allows the attacker to gain access or run malicious code. In e-commerce, malware can allow attackers to access your customer database, stored credit card information, or personal location data. If you secure your own servers, you have to be diligent about permissions, but even on third-party platforms, malware is a serious problem. For example, WordPress plugins can bring malware into your application.
- SQL Injection – SQL injection is a technique in which SQL statements are added to existing queries in your application. This allows attackers to gain access to your database without your knowledge. While most modern frameworks guard against SQL injection, custom codebases have to be especially careful of this vector.
- Brute Force Attacks – If your e-commerce store’s admin login is publicly available on the internet, attackers can simply attempt thousands of likely passwords in an attempt to log in. Many third-party tools guard against this threat, but if you’re building your own authentication system, you need to be sure this vector is handled.
These general security threats apply to almost any e-commerce application or platform, but many attacks are specific to the platform you use. In the next section, I’ll share more information about some of the e-commerce platforms you might use and how these attacks might manifest on each of them.
[toc-embed headline=”The Build vs. Buy Decision with E-Commerce Security”]
The Build vs. Buy Decision with E-Commerce Security
If you would like to have more flexibility and control over your e-commerce platform’s security, it makes sense to build your own application from scratch. However, the cost and time required to do so make this an untenable option for many businesses.
On the other hand, you can use a third-party platform to power your digital storefront. In this case, the platform will handle most major security concerns and give you a scalable, well-tested piece of software to run your business on. Leveraging a third-party e-commerce platform seems like an obvious choice, but there are security risks inherent in this decision as well.
Security in a third-party e-commerce platform
If you’re licensing an existing e-commerce platform, you probably don’t need to worry about managing SSL certificates, detecting fraud, or many of the common threats above. A reliable e-commerce platform will keep an eye on security issues and deploy fixes automatically as problems are found.
That said, no third-party platform is perfect. Magento and Shopify—two of the biggest e-commerce platforms around—have both suffered from data breaches in the past year, so you can’t blindly trust big providers.
In fact, some vulnerabilities are more pronounced in popular third-party e-commerce platforms. For example, if you’re using a platform that allows external themes or plugins, it’s impossible to monitor every line of code they bring in.
If you’re using a platform like Shopify Plus, you won’t get access to the source code or even know when updates are made. This means that vendors can maliciously or accidentally inject vulnerabilities into your store at any time, and you’ll have no way to know where the attack came from.
Security in an in-house e-commerce application
On the other hand, security isn’t any easier when you build your own store from scratch. It’s just different.
Instead of relying on a third-party provider to manage backups, prevent fraud, or stop XSS, you’ll have to handle this yourself. While it won’t take all the pressure off, you can mitigate some of the above risks by using a well-known framework and a third-party payment gateway. This way, you can at least minimize your risk of the most common e-commerce vulnerabilities.
Building your own e-commerce platform from the ground up gives you the most control over security and scalability issues, but it’s the most expensive and complex solution from an engineering perspective.
Security with a hybrid approach to e-commerce
Another pattern you might want to consider is using third-party vendors for parts of your e-commerce application and your own services for other parts.
For example, you could use a headless e-commerce platform like fabric to power your product information management system (PIM), a third-party authentication provider like Okta, a specialized payment processor like Stripe, and an in-house shipping and warehousing service.
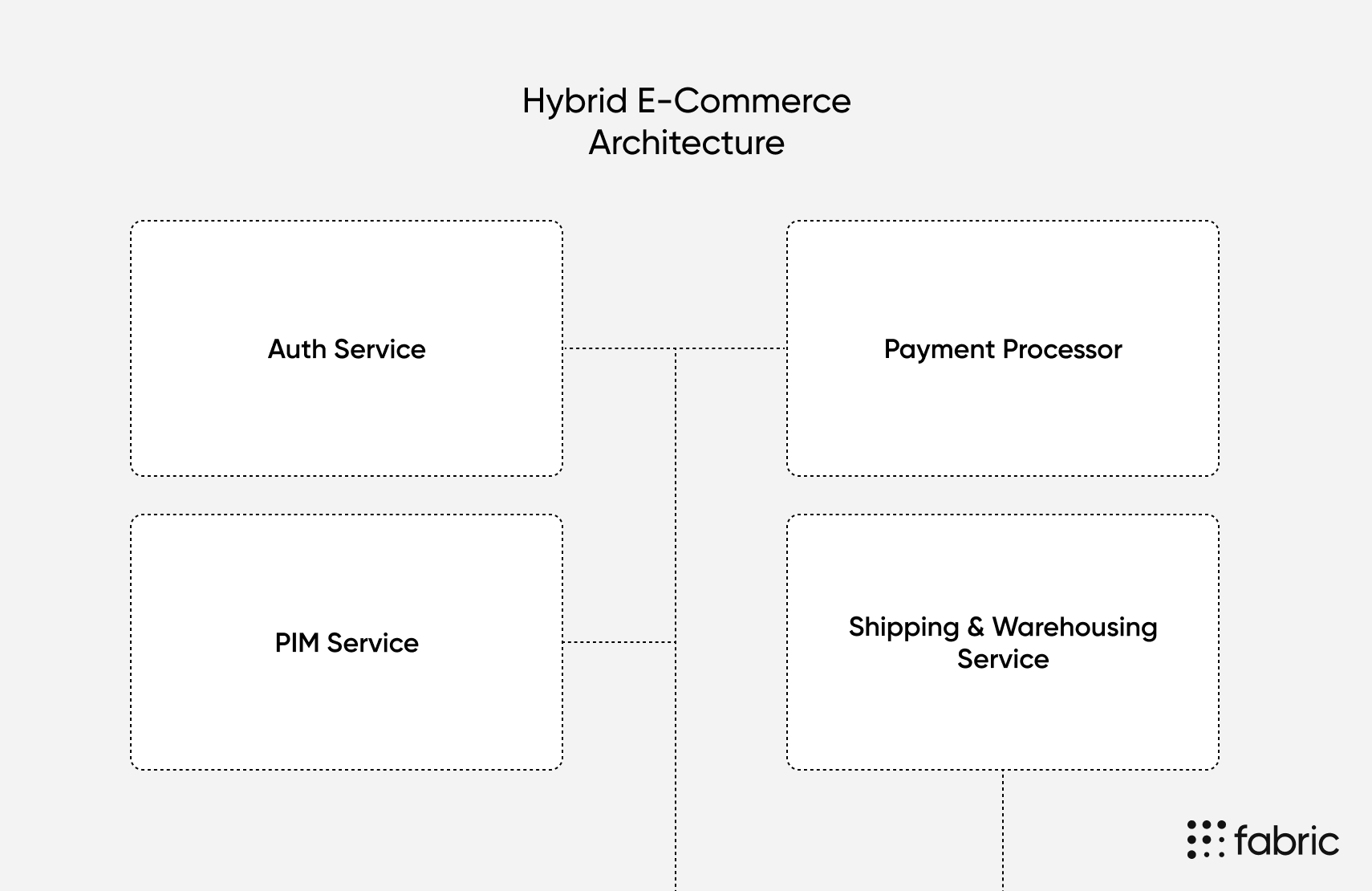
This hybrid approach offers several advantages from a security perspective. You can offload the riskiest parts of your security to third-parties that specialize in these areas while keeping custom code in-house. You can also maintain control over the networking between these services so that users who access your store can’t see all the inner-workings of your architecture.
This extra layer of obscurity slows down attackers and ensures that you aren’t vulnerable to the same attacks as every other customer on these third-party systems.
[toc-embed headline=”Best Practices for E-Commerce Security”]
Best Practices for E-Commerce Security
If you’re building your own e-commerce platform from the ground up, be sure to adhere to all the best practices here. But if you’re evaluating third-party vendors, you have to be vigilant as well. You can’t assume that every e-commerce platform makes security a priority, so do your homework and ask the tough questions.
Here are seven best practices for e-commerce security to keep in mind as you build or buy your online store:
- Avoid Storing Sensitive Data – Refrain from storing sensitive customer data (e.g., credit card or banking information) as much as possible. Attackers can’t steal what you don’t have.
- Use Trusted Payment Processors – The most valuable data you will have is likely credit card information for your users. Whether you store it yourself or pass it to a third-party service, make sure every link in the payment processing chain is reputable and adequately secured.
- Understand and Comply with PCI-DSS Requirements – If you’re storing or passing payment information, pick a PCI-compliant hosting provider. PCI compliant hosting providers have stringent security policies and measures for ensuring safe and secure payments.
- Use HTTPS and SSL Certificates – Secure Socket Layer (SSL) encryption ensures that data in transit cannot be read by attackers. This keeps your microservices, backend, and form input data secure.
- Use Two-Factor Authentication – Whether you manage authentication yourself or use a third-party tool, two-factor authentication will dramatically improve your application’s security. According to a study by Symantec, two-factor authentication would prevent 80% of data breaches worldwide.
- Keep Your Platform, Frameworks, and Libraries Updated – Unpatched software and extensions make your e-commerce website vulnerable, especially if you’re maintaining your own custom software.
- Use a Content Delivery Network – A Content Delivery Network (CDN) caches content to reduce page load time, but it also acts as the first line of defense against DDoS attacks on your website.
[toc-embed headline=”Conclusion”]
Conclusion
Trust is critical in getting customers to buy from you and keep them coming back. It takes a long time to build trust, but it can be eroded in minutes when you have an unreliable or insecure online store.
While security is everyone’s job, software development teams have an outsized role in building a secure application, so they have to be especially diligent. Whether you build your own e-commerce platform, purchase one from a trusted third-party, or employ a hybrid approach, make security one of the key parts of your evaluation and implementation process.
Finally, if you’re looking for a secure, scalable e-commerce backend, check out Fabric. Our headless, microservice-based approach takes critical security risks out of your hands while giving you the power and flexibility needed to build great buying experiences.

Content marketer @ fabric. Previously marketing @ KHON-TV and Paramount Pictures.